Camera Cyber Lockdown Feature
White Paper by Dean Drako, CEO of Eagle Eye Networks
The PDF version includes additional content; download for more on this subject.
Overview
Eagle Eye Camera Cyber Lockdown is a set of cyber security features that have been released as part of the Eagle Eye Cloud Security Camera Video Management System (VMS). The purpose of Eagle Eye Camera Cyber Lockdown is to significantly reduce or eliminate the impact of camera cyber security issues.
Protecting network video surveillance cameras is important because many cameras have multiple cyber security issues:
- Cameras are manufactured by many companies located all over the world. Many of these companies have unknown political and governmental affiliations.
- Many cameras are manufactured by one company, then labeled and sold by different companies. It can be difficult to determine the manufacturer and country of origin.
- Many camera suppliers and manufacturers are lax on cyber security—they do not perform adequate testing of their cameras and do not have the knowledge required to make their cameras truly cyber secure. It is hard to determine camera cyber security profiles when selecting cameras.
- Manufacturers may have accidentally or on-purpose included secret “backdoor” access to cameras.
- Many camera manufacturers do not address discoveries of camera cyber security flaws in a timely manner, by providing firmware upgrades addressing the security problems. Some do not provide firmware upgrades at all.
- Often the published factory default passwords are not changed when cameras are installed, or easily- guessed passwords are used, leaving cameras wide open to individual hacker intrusions and automated network-based attacks.
- Passwords are often transmitted in plain text and thus are discoverable.
- Upgrading firmware on a large quantity of surveillance cameras is generally labor-intensive and costly.
- Many surveillance camera customers (end users) do not have processes in place to monitor the discovery of camera cyber vulnerabilities and to perform camera firmware upgrades when they are released. Their cameras remain vulnerable.
The Problem
Part 1: Internet Connections
A “bot”, short for robot, is a software program that performs automated tasks. A botnet is a network of computers, each of which is running one or more bots. Hackers have coopted the term “botnet” to refer to a network of internet-connected devices, including PCs, servers, mobile devices and internet-of-things devices, that are infected and controlled by a common type of malware, with the device owners usually unaware of the malware infection. Internet-connected security video cameras and recorders have become a favored target for hacker botnet infections.
In September and October of 2016, the two largest global botnets attacks to date were launched using several hundred thousand infected cameras, digital video recorders (DVRs) and network video recorders (NVRs). Researchers have reported that in 2016 about one million web-connected video cameras and DVRs were infected by malware, with most of the camera and DVR owners unaware that their devices are infected.
The root of the problem is the desire of individuals and businesses to remotely view security video using a desktop or laptop computer, tablet, or smartphone. Traditional DVRs and NVRs require a connection FROM the Internet to the recorders (see the red lines in the image below). If the recorder does not have an Internet connection, video can only be viewed at the recorder’s location, and few customers are willing to accept a restriction to local viewing only.
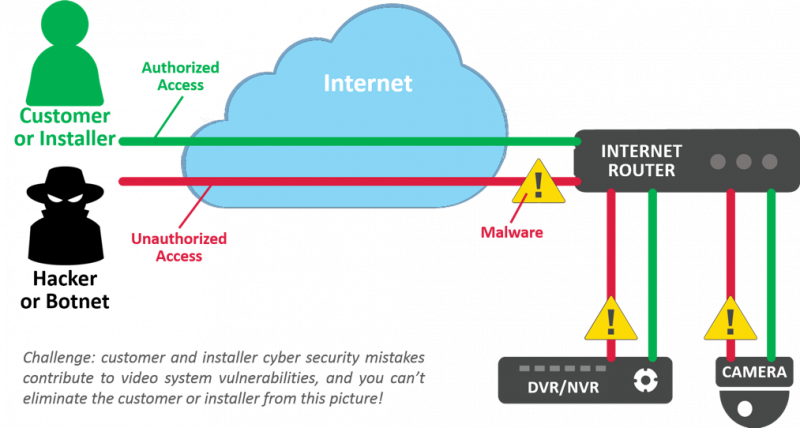
Cameras, DVRs, and NVRs have little to no protection from cyber attacks, very few have built-in firewalls. Most have not undergone adequate cyber security testing by their manufacturers or installers. Most have major password vulnerabilities. Few receive adequate firmware upgrades to fix security vulnerabilities or have their operating system (OS) vulnerabilities patched as updates are released.
In July 2017, cyber security researchers discovered a serious flaw, which they named “Devil’s Ivy”, that exists in nearly all cameras supporting the popular ONVIF specification. The flaw allows hackers to take full control of ONVIF-compliant cameras. Most camera makes and models are vulnerable, including top brand high-quality cameras. Within days a few major manufacturers issued firmware updates that correct the flaw. It is up to camera owners and servicing contractors to update the cameras. There is no telling which manufacturers will make firmware corrections for their cameras, or how many of the millions of vulnerable installed cameras will actually be updated.
When vulnerable cameras and recorders can be contacted directly from the Internet, they can be easily attacked and exploited by cyber criminals and other attackers. Strong cyber security controls and constant vigilance are needed to avoid recorders being compromised. Any device connected to the Internet is typically attacked or probed hundreds of times per day, especially DVRs and NVRs, as they are a high-value target.
Part 2: Trojans, Spyware, and Pre-Installed Viruses
There is a significant concern that cameras, DVRs, and NVRs may be provided by the manufacturer or the installer with spyware, Trojans, or viruses already installed. There are many documented cases of this having occurred.
When that occurs, the device is running software that will either immediately, or at some predetermined future point in time, attempt to contact a “command and control server” (CCS) on the Internet to retrieve additional software code and instructions. For example, a compromised camera could have a Trojan that will attempt to contact its CCS on January 15, 2019. On that date, the camera will use the Internet connection to obtain instructions from the server.
Most networks allow outbound connections from any device on the network. More sophisticated network configurations utilizing VLANS or firewalls will attempt to block outbound connections, but this is not the norm. In a typical network, encrypted outbound connections to a CCS would be allowed. Files from computers on a local network, video images, and passwords could easily be transferred out to hackers by an infected camera. The camera could then receive instructions and additional software to execute, to hack into other computers on the network, attack databases, transfer out credit card information, or take part in a denial of service (DDoS) attack.
In the case of the Trojan or pre-installed virus on a camera, NVR, or DVR, the infected device simply needs ANY access to the Internet to become part of a botnet and pose a serious threat to the systems the controlling hacker has targeted.
Why Hackers Attack
The days of kids hacking websites just for fun are long gone. Hacking is now a big business that steals information to sell it and uses encryption to hold websites hostage for ransom. These websites can be of any type, including public-facing websites, gaming systems, e‑Commerce sites, and in some cases even government systems.
Key hacker objectives include:
- Obtain confidential personal information such as credit card numbers, social security numbers and other personal identification information (PII).
- Obtain confidential company-related information such as customer information, financial statements, etc.
- Bring down a website or network via a distributed denial-of-service attack (DDoS) by utilizing a botnet of tens or hundreds of thousands of compromised devices (often distributed globally).
DDoS attacks have become the most prevalent type of attack, growing rapidly in the past year in both number and volume. Network cameras, DVRs and NVRs are an ideal target. Their vulnerabilities make for a highly insecure system that is simple to exploit.
Are you interested in the solution? The remainder of this paper explains Eagle Eye’s Camera Cyber Lockdown.




